If your business is still running on the same cybersecurity approach that you’ve always followed, it’s time to rethink and reevaluate your security program. There are new things to learn about and ways to harden your network that can help prevent even more threats from entering the system. One of the tools that you need to examine is the NIST cybersecurity framework.
So what is the NIST framework? It’s a framework that helps organizations improve their cyber posture. The framework is especially useful in setting up cybersecurity programs and improving readiness against cyber threats.
The National Institute of Standards and Technology (NIST) issued its first cybersecurity framework in 2014. The first update, published in February 2016, includes more than 25 actionable items that organizations can use to improve their cybersecurity posture. The NIST cybersecurity framework is a part of an ongoing effort by the U.S. Department of Commerce’s National Institute of Standards and Technology (NIST) to improve the nation’s network security.
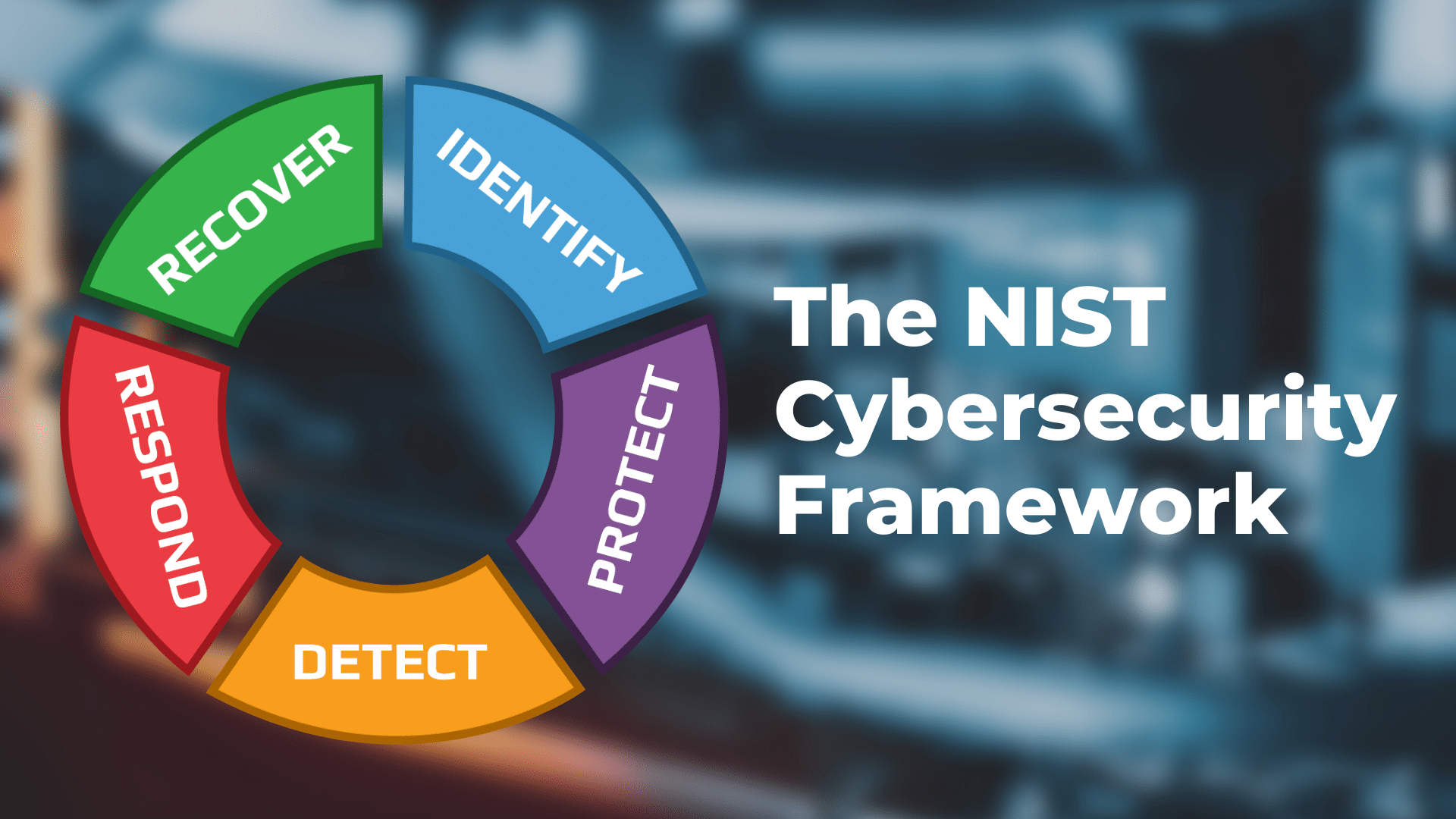
The NIST Framework Has 5 Core Functions
Identify
The first element is centered on laying the foundation for an effective cybersecurity program. This would include doing a risk assessment to determine where vulnerabilities lie, making a list of all devices in your organization (including laptops, desktops, smartphones, and tablets), and documenting where your most sensitive data is stored.
Protect
Protecting information involves controlling who is able to log onto your network and use your devices. It also means using good security and anti-virus software that update regularly and automatically, encrypting data, and backup of your data via a local backup or cloud backup.
All employees should have a formal security awareness training program to complete. Human error is the biggest way that data can be leaked. Policies should also be in place for disposing of computers that are no longer in use.
Detect
Being able to detect when your data has been leaked is something that most companies only find out after it has happened. In order to detect a breach or when information is being sold on the dark web, you need to have breach detection software and dark web monitoring in place.
Endpoint detection and response (EDR) software is also extremely helpful for noticing any strange behavior on employee machines.
Respond
Despite having the best protection against an attack, a breach can still happen and has happened to companies that are worth billions of dollars. Having a tightly knit response plan can greatly mitigate the damage an attack can cause.
Recover
The final step is to get things back up and running after a cybersecurity event. Getting your network and equipment restored and informing your employees and customers what is being done to recover is crucial.
Why Should Small Businesses Be NIST Compliant?
The NIST framework can be implemented by any business to lessen their cybersecurity risk. Having the proper security protocols in place is not just a one-off solution and requires a continuous approach. If your business can prove that you follow the framework, you will be trusted by your clients and partners by showing that you have a plan to bounce back from a catastrophic event if it occurs. You can also use the NIST compliance status as a marketing advantage to edge out your competitors.
Next Steps
We hope that this overview of the NIST framework has helped to simplify not only its uses, but also its benefits for you and your business. Whether you’re a new business looking to protect yourself and your data, or a more established one wanting to further secure your digital infrastructure, the NIST framework can help make that task easier. It’s not something that you need to take on all at once—but it’s an important process to put in place, and regularly revisiting is always a good idea.
If you’re wondering how exactly to go about making your business compliant with NIST framework standards, reach out to us for help!